
May 28, 2013
The API are now becoming more used every day.
Today every major website provides it’s own set of API and often the company websites and services are chosen (or not chosen) based on the availability of API and their design.
In this huge world that is getting bigger every day, RESTful API plays a huge role, in fact a lot of companies are moving their API to RESTful API since it’s easier to use, therefore more attractive for potential clients.
Read More 
May 7, 2013
The anonymity on the web is probably one of the most debated topics on the web.
Is possible to be completely anonymous? The short answer is no.
This book tries to help the read to improve its anonymity, staying is the “real world”, as the “Practical” world in the title suggests.
In this book you will not find anything that is too complex for an average user.
Whether this is good or bad, depends on you expectations. I’ve took this book the first time with really high expectations and I was really disappointed. When I took it for the second time, with different expectations, I did found the book pretty good.
Read More 
April 16, 2013
Mike Shema speaks about a lot of different kind of attacks in his book in a real deep way, at the point that sometimes I wondered if he was planning to instruct people how to hack websites or only how to secure own websites. The book has often some code samples that allow a faster understanding of what the author is saying. Even if a coding knowledge is not required, the ability to understand HTML, JS, SQL, PHP, Python and C++ speeds up the reading.
Read More 
April 2, 2013
As the name suggests, this set of videos is for developers.
HTML 4 and Javascript are often used without much explaination about the JS code it self but only about the HTML5 Canvas part.
I felt to point this out immediately since I’ve not found it on the O’Reilly page, but I believe that is really important to specify.
Another thing that I’d like to point out is that (as it is easy to imagine, but not obvious) these videos only speak about 2D graphics in HTML (therefore there will no WebGL topics).
After these two notes (that will not influence in any way my judgement about the videos), let’s start talking about the videos.
Read More 
February 28, 2013
Today I would like to give you an idea on how to implement a spam system that can reduce some kind of spam.
The problem
Sometimes a company or a politician, that does not respect the usual privacy policy, continues to send e-mails even if the user already tried to unsubscribe.
My postulates
- The people who usually send this kind of e-mail are not very familiar with how e-mail work or how the privacy policy works. Obviously there is the case in which they are malicious, but I prefer to think that the biggest part of these people are in the first two cases.
- These people probably will have issues removing a person from a mailing list, therefore they will tend not doing it, unless they have an advantage.
- Is really annoying sending an e-mail to 10 contacts and receive 8 mail-delivery-subsystem errors.
My approach
My approach is dividable in two directions that have to be implemented as features from the e-mail provider:
Read More 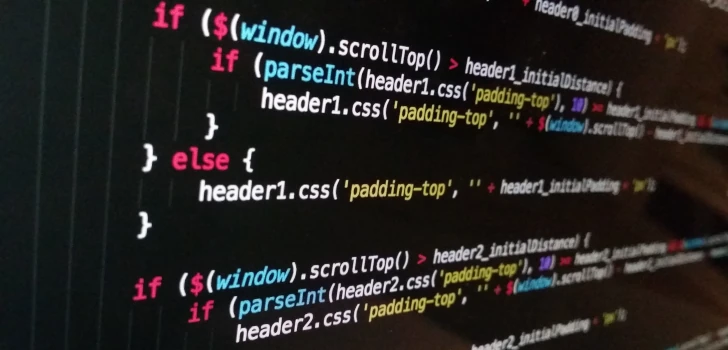
April 17, 2012
jQuery has very interested me in the last period.
I think that it is the best JavaScript library for me.
jQuery UI is a set of functions that allow you to improve the graphics and the functionality of your websites with very few lines of code.
My jQuery level was pretty close before I took the time to read this book.
I’ve found this book amazing and really interesting even for fast-learner as I am (knowing a dozen of languages and libraries I tend to go really fast when I’m studying a new language or library).
I think this book is mainly for beginner or intermediate users since it focuses the reader on the main parts of jQuery UI leaving aside some real-world and advanced coding details that may be crucial in the real world development.
Read More 
April 4, 2012
Since the four authors are very popular in the SEO field, I was expecting the best book on SEO ever. All my expectation have been met.
I think that the book authors have done a great job describing these difficult concept in an easy and ordered way.
The book, also, is very complete.
The touched topics include: user-focussed data, key analytical tools, effective website creation, result tracking, search engine theory and behaviour, the impact of social media, SEO best practices and much more.
Sometimes the authors deviate from the topics usually covered in SEO books, in fact you can find topics like In-house vs outsourced SEO.
Read More 
April 1, 2012
jQuery Mobile is a library that allows you to develop mobile apps using jQuery.
Is even possible to use a jQuery Mobile program as a native app, thanks to programs like PhoneGap.
This book assumes that you already know jQuery and I think that this is good since the author can focus only on the main topic in this way.
I think you should know or study jQuery before even starting this book.
I do know that’s possible to understand jQuery code even if you don’t know anything of JavaScript if you have rock solid programming knowledge, but I discourage it.
Read More 
February 28, 2012
Mining the Social Web is a good start for anyone is going to create scripts to analyze patterns in Social Networks.
I’ve to say that this book consider that the reader already masters Python.
I think that should be written directly on the title (ie: “Mining the Social Web with Python”).
I liked the really fast approach to the Social Networks, even if a lot of times I wanted more; for this reason I consider it only a start, not a complete book.
Read More 
December 6, 2011
Gordon Lyon (also known as Fyodor), the creator of Nmap, sent an email yesterday to the Nmap mailing list pointing out that the C|Net Download.com website is altering Nmap downloadable files injecting malware into them.
It’s also possible that other files delivered by C|Net Download.com are also subject to the same problem.
This event is a very problematic one since it will create a complete loss of trust toward Download.com.
It also reminds us of a critical aspect of security: all chain steps need to be secure and trusted.
Read More 








